Trying to remember the password for all of your different web interfaces?
Remember one less password, by enabling AD (Active Directory) authentication for phpIPAM.
This is an article in a series or articles, about configuring phpIPAM for automation.
If you want to know more about this, you should read the previous articles.
Previous Articles
Free IPAM solution – 1. Installing phpIPAM
Enable SSL on Apache2 (Self-Signed)
Otherwise just read on.
All the following step presume that you installed phpIPAM like demonstrated in article one on Ubuntu 16.04
Setup
Step 1 – Install Prerequisites
To get Active Directory support in phpIPAM you have to have the ldap php module installed. Run the following command as root.
# Command: apt-get install php7.0-ldap service apache2 restart
Step 2 – Setup Active Directory Service Account
To authenticate users using Microsoft Active Directory you need a service account. This should be an ordinary AD User account. No reason for administrative privileges. I have called mine “service_phpipam”
Step 3 – Add Root Public Key to trusted CA’s
To get SSL/TLS working you need to have phpIPAM trust the certificate your domain controller is using to encrypt your LDAP traffic. Your Ubuntu server will not get your PKI Root servers public key from Active Directory automatically, so we need to add it manually. First you need to get it. If you are using a Microsoft CA server it is most likely located in a share on that server called CertEnroll, otherwise you will most likely find it on any domain joined client.
To extract you Root CA certificate from a client do the following.
- Open a RUN box by pressing Windows-Key + R
- Type MMC and press ENTER. Agree to any UAC prompts.
- Press Control + M to add a snap-in
- Select the Certificates snap-in and press Add
- Select Computer account and press Next
- Choose Local computer and press finish
- Press OK
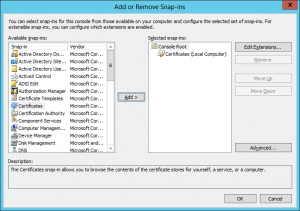
- Expand Certificates -> Trusted Root Certificates Authorities -> Certificates
- Find you Root CA Certificate and Export it in Base-64 format
- Open the file in notepad or any other editor.
- Copy the contents into your clipboard
- Paste the contents into the end of the file /etc/ssl/certs/ca-certificates.crt on your phpIPAM server.
- Restart Apache2 service
# Command service apache2 restart
Step 4 – Configure Active Directory authentication
Go to Administration -> Authentication methods as admin in phpIPAM
Click Create AD authentication, and fill in the relevant information.
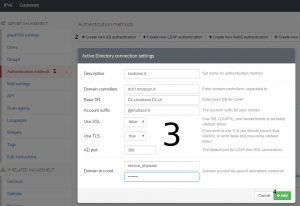
If you have not setup a PKI infrastructure and have not deployed SSL certificates to your domain controller and you phpIPAM website, I strongly recommend that you stick to local users, as your login information will not be encrypted. If this is a test environment with a test domain, you can just deselect TLS.
Step 4 – Add users and/or groups
Now it is time to test if you can add a AD user to phpIPAM.
- Go to Administration -> Users
- Click Create User
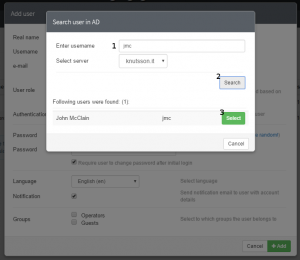
- Click the Magnifying Glass

- Search for your user

- Select the User
- Enter an e-mail address. It does not have to exist.
- Choose user Role
- Disable Notification
- Click Add
If you do not want it to send E-mail, disable Notifications.
In order to use E-mail notifications, you will have to setup E-mail under Mail Settings. As this is very easy I will not be going through it at this point. If you enable notifications, and have not setup mail, you will get an error.
Now logout and check if you can login with the added user.
You are done.
Next step
Setup REST API for automation with vRealize Orchestrator. (Coming Soon)
Troubleshooting
I found in one case, when installing on CentOS 7, that Active Directory communication was not working, but gave an error.
The error was: Permission denied (13)
The error is due to selinux protections, to disable this protection you need to execute the command: “setsebool -P httpd_can_network_connect 1” as root in the console.

I’ve configure AD authentication but it seems to accept any password if login matches AD login.
Huh. I have not had that issue. Could you post a screenshot of you AD config somewhere?
I’m trying to setup ldap connection to openldap server, however I keep getting an Invalid credentials, I will appreciate if you can help with this
Have you resolved the issue?