So you have migrated to NSX-T 3.2 and you are using IDFW rules to allow users to dynamically gain access when they log in to any physical device in the domain.
Only trouble is that now it is not really working, and VMware did not yet implement a way in the gui to see the effective members of Groups that contains Active Directory members.
Well there is a way you can see who is in the group at least, but there are a couple of steps.
How to find the effective group members
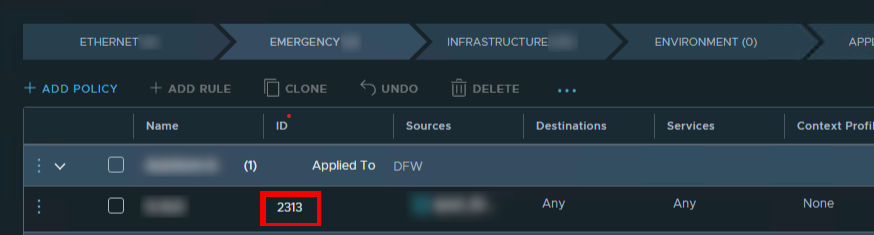
Step one is to identify the rule you are troubleshooting. Make a note of the rule id.
Next find the host the destination VM is running on. You can do this manually in vCenter or use powershell. That’s up to you.
Continue reading NSX-T Troubleshooting IDFW rules